
Are you surprised that your supervisor keeps nagging you whether your firm is resilient to cyber attacks and what your plans are with NIS2 regulation behind the corner? If this sounds familiar, keep reading. Because we’ve released a handy report for CISOs of all organizations - the Citadelo Ethical Hacking Report 2023 - and in it, info on the 2,795 vulnerabilities we found. Leading the Web, Cloud and Infrastructure. After reading it, you won’t be surprised with your supervisor anymore.
Let’s go in order and take a look at the basic data we collect. At first glance they may seem ordinary - the number of projects and their types, the number of vulnerabilities and the types of the systems tested, are nothing shocking, but this “ordinary” data and its collection helps us to accurately identify the weaknesses of your companies and the systems you use. Click HERE to download our full report.
The number of critical vulnerabilities grew by 4% last year, with just 1 critical finding marking catastrophic consequences when hackers attack, whether in the form of RCE - Remote Code Execution, Privilege Escalations or the ultimate goal in hacking companies, gaining the role of - Domain Administrator, which opens the door to endless possibilities for the hacker.
Overall results for 2023
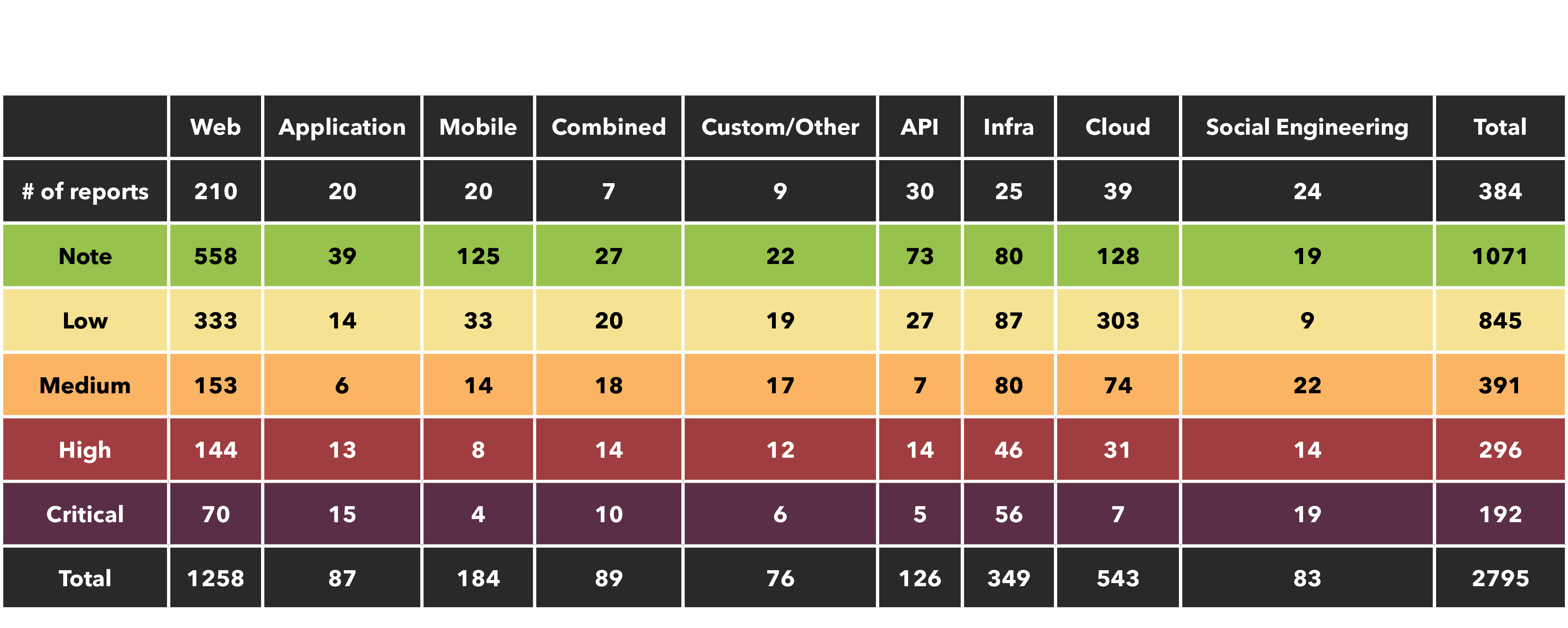
Chart showing project types and rating of vulnerabilities found, from note to critical. Download the full report HERE.
The real impact of these numbers can be staggering, as with SQL injection on the web, a hacker can read all your internal data from the hacked database. You may have passwords, client data or sensitive data stored on them which is then in the “power” of the hacker. This is just one of the many loaded possibilities of exploitation by a hacker with a critical vulnerability. So you see, these are “just numbers” and statistics but we can see and we want you to see what they mean and what’s really behind them.
Chances are that as you are reading this, one of the systems named is the one your business or its management runs on. That’s why it’s important that you understand what our data shows and the real impact it has on you and your business.
If your business is built on the web, from our data, this is the most vulnerable type of system in terms of the number of vulnerabilities found. We also found the highest number of critical vulnerabilities in the web - 70. What does this mean in practice? We mentioned RCE above, another very threatening possibility is the scenario called SQL Injection, where a hacker can read your internal data from the compromised database - whether you store client data, passwords or sensitive information. It’s important to note that just as a hacker can read and access data on a database, they can also read and delete it all.
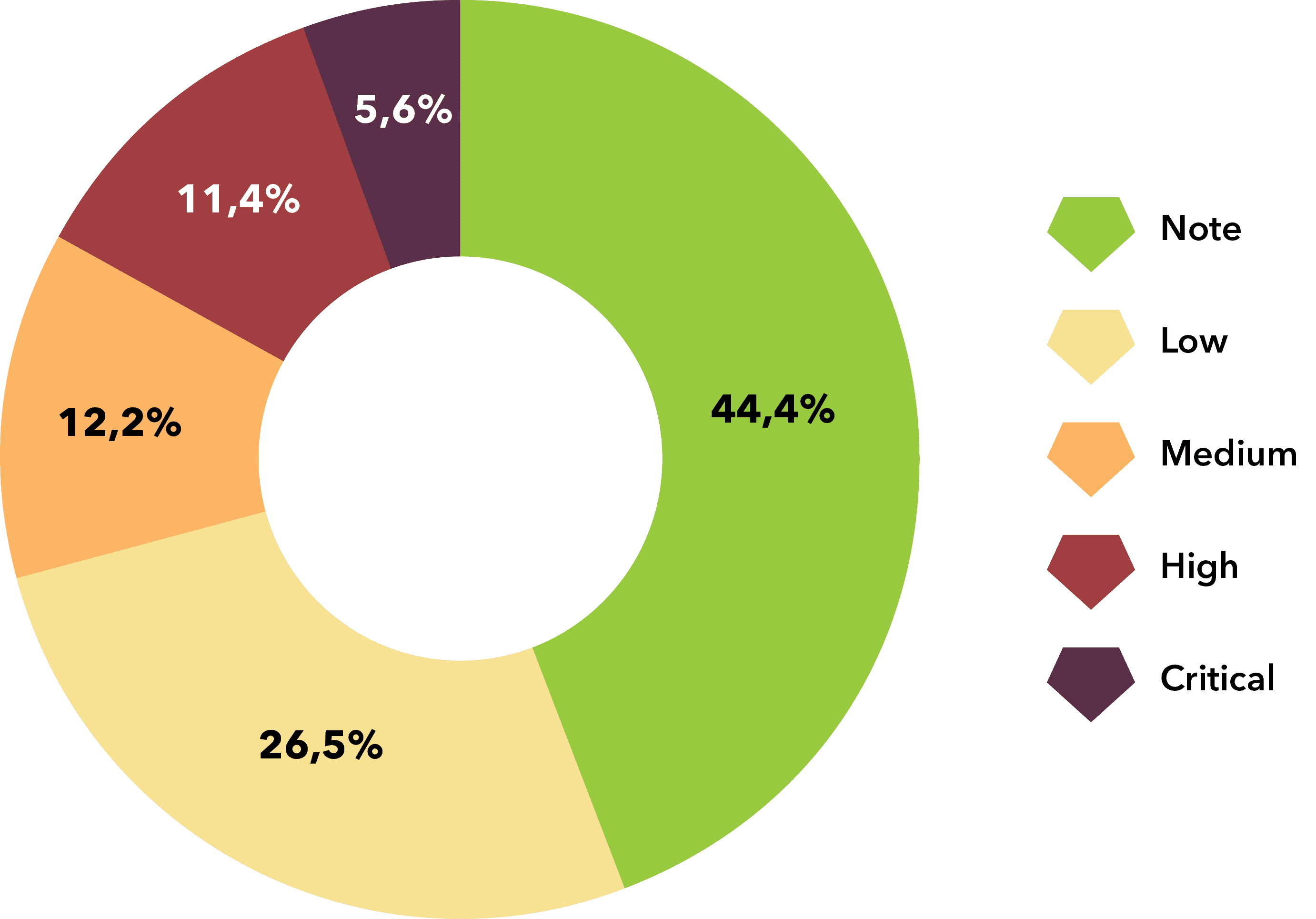
Types of vulnerabilities found from note to critical in Web.
As the web may be publicly accessible, its vulnerability or possibility of attack is several times more probable so with this risk the chance of exploitation increases. The problem often lies in web development when the idea of Security Best Practices is something that is absolutely not considered. This then opens the door for hackers to abuse the site in various ways - generating discount codes or exploiting shopping carts where attackers are able to shop for free or obtain shopper data. The possibilities are really many, it depends on the creativity of the hacker.
If your business is built on the Cloud, our report shows that it comes out as the second most vulnerable type of system by the number of vulnerabilities found. One of the worst situations in a Cloud system is Privilege Escalation, i.e. the misuse of one user role in the system for completely different purposes and with completely different powers, the goal being to get to the highest level of power again. This is the equivalent of a domain administrator who manages the entire network and can authorize the transfer of data, disclose any necessary information to the hacker, or from this position himself authorize the transactions or transfer of sensitive data. In this position, creativity really has no limits.
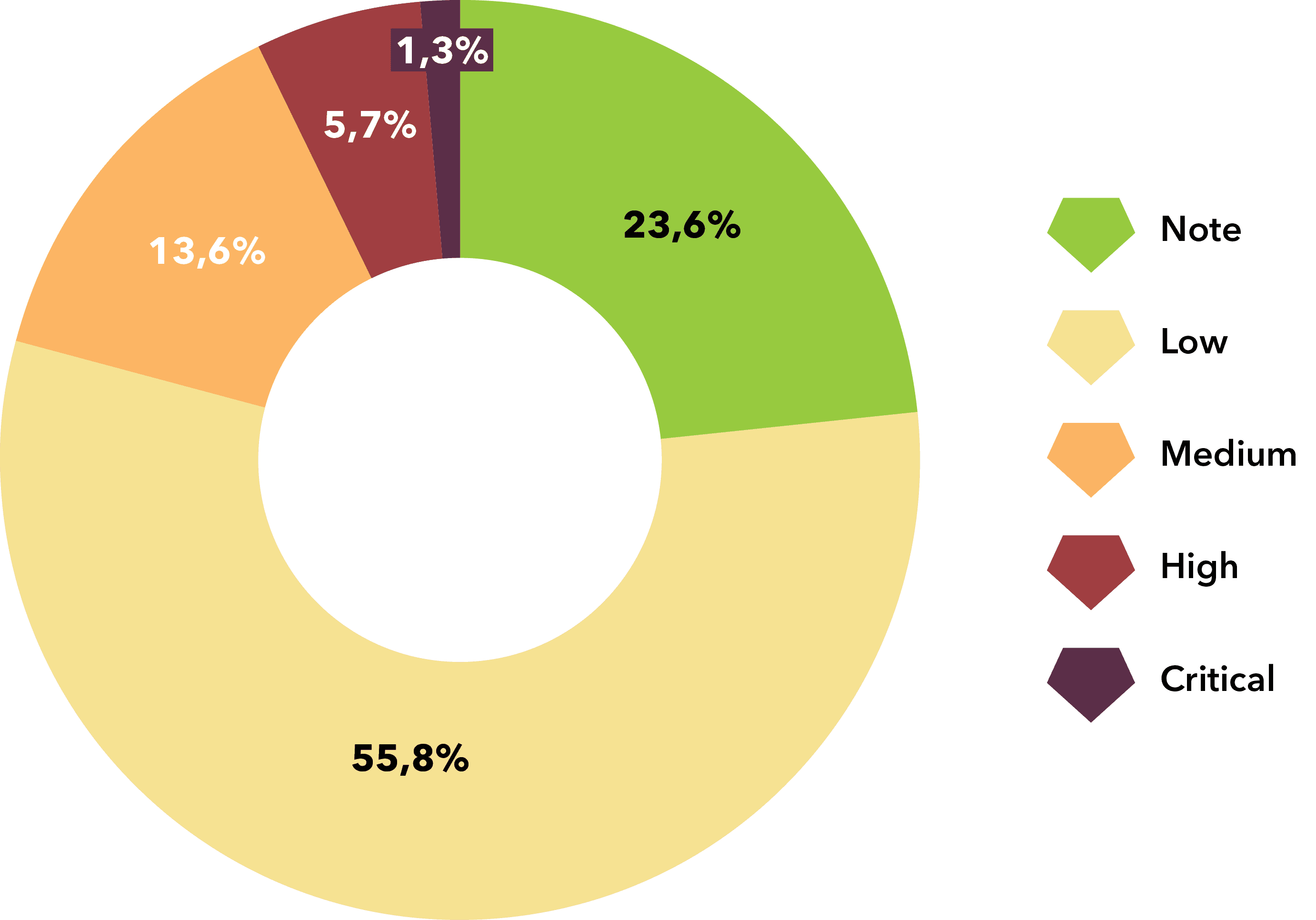
Types of vulnerabilities found from note to critical in Cloud.
There is a high chance of vulnerabilities in the Cloud due to the fact that there are a lot of options for role settings and the system in general, which unfortunately are very poorly granted and ranked according to Security Best Practices, which in turn gives us a lot of options and steps that we can exploit.
For internal infrastructure, little emphasis is placed on the need for cyber security, as it is assumed that only employees have access to that infrastructure, thus we find many holes and a greater number of vulnerabilities. However, it is important to note that just like us - ethical hackers, a black-hat hacker (e.g. by phishing) can get into the internal infrastructure and will not be able to choose what to exploit first.
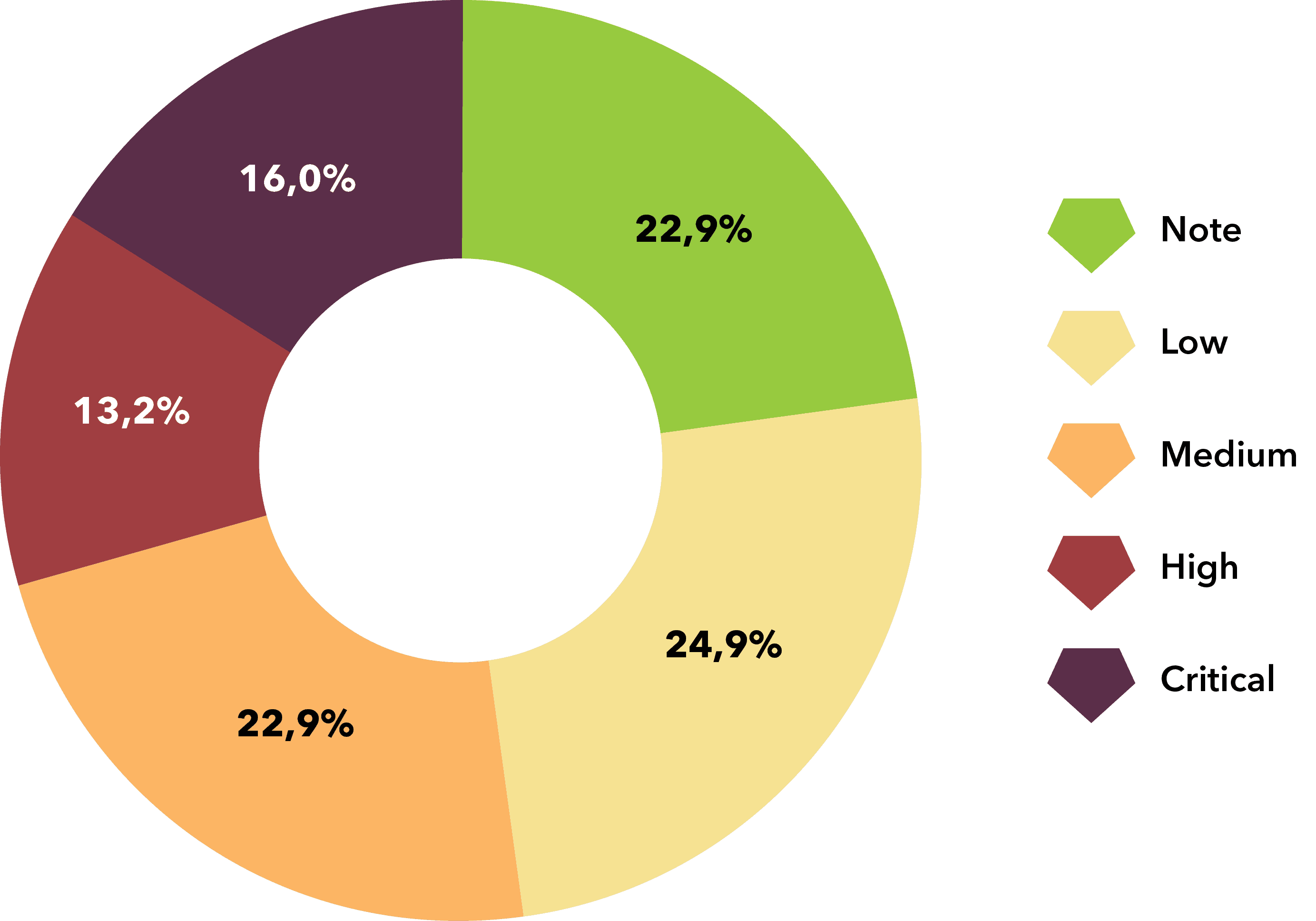
Types of vulnerabilities found from note to critical in Infrastructure.
If your business is built on Infrastructure - internal or external, it is one of the TOP 3 most vulnerable systems - by number of vulnerabilities found. Similarly to the Cloud, the worst case scenario is the so called Escalation of Privileges to the Domain Administrator, which can mean a complete compromise of the internal network - a common situation is when an attacker exploits ransomware - encrypts the acquired data with a key that he is willing to sell to the client for a hefty sum, or threatens to disclose sensitive data if the client doesn’t pay the required amount.
In most cases, this is a method and vulnerability that is simple and will not give the black-hat hacker much trouble to misuse, so we also place a lot of emphasis on smaller vulnerabilities that accumulate and consequently can be the equivalent of a critical vulnerability.
However, it is not always the system that is not sufficiently secured and therefore we cannot fail to mention the human factor, which led and still leads as the most successful vector of black-hat hackers’ success. Compared to 2022, we saw a 4.5% increase in demand for Social Engineering testing, which we’re happy to see, but we know it’s a very small number compared to how often these types of attacks occur in the world.
For this reason, we educate with Employee Training and if the budget is larger, we provide comprehensive Red Teaming, which includes:
Then with all the information gathered we try to achieve the worst case scenario.
Of course, all of these situations and vulnerabilities can be prevented by making the business and clients understand the importance of the difference of being hacked first by an ethical hacker and pinpointing the holes in cyber security and then knowing what needs to be secured - rather than when a black-hat hacker gets the first chance. We always apply the gold standard - a follow-up re-test that verifies the applied and “patched” cybersecurity holes so the business and clients can sleep soundly.
Click HERE to download the full report and our data.
Want to know how many vulnerabilities are in your system? Contact us today and turn your weaknesses into strengths!
