
13 July 2018 / 4 minutes of reading
Malware trends in 2018- Ransomware left behind by mining viruses
This blog is about CoinHive. I will describe how it affects websites, how websites get infected and how to prevent it or how to get rid of it.

Introduction
This blog is about CoinHive. I will describe how it affects websites, how websites get infected and how to prevent it or how to get rid of it.
How many websites are affected?
You might ask yourself how many websites are affected for example in Czech Republic? Unfortunately, there are about 4 000 websites infected with CoinHive. There are many websites affected by this malware worldwide, but some website owners are not even aware that their website already contains this malware. The lack of security in general can allow this malware to be installed on your website’s host server without you even noticing it in time.
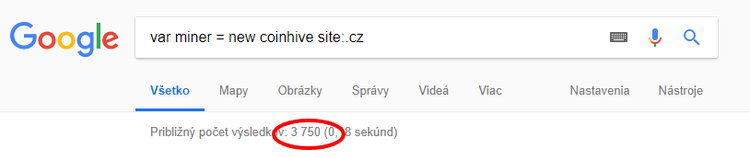
What types of websites are targeted?
Different types of websites are targeted, but mainly those ones with less security and with good amount of audiences. For example, even photography sites are targeted for this reason. Once infected websites connect to the webserver, it will kick visitor’s computer with malicious mining tool which allows the attacker to mine on viewers computers. With this method the attacker group will be mining a cryptocurrency and could be making a lot of money using the viewers hardware. Websites are not targeted randomly. An attacker will search for a weak webserver (which means weak security) and once the website with a weak web server is located by the attacker, he will hack the server system and inject the website files with malicious mining system. It’s not only websites that are targeted. Similar malicious mining systems were also detected on thousands of mobile applications, mainly on Android.
Why is CoinHive used?
This process is used by the attacker groups to make money illegally and anonymously. The CoinHive system uses currencies such as Monero, which are untraceable and used for anonymous transactions. CoinHive will invest into cryptocurrencies for free using other people’s hardware “computers” to mine without their permission through their browser. CoinHive is used for breaching security and leading hackers hijacking cryptocurrency mining scripts on some known or legitimate websites. This malware will then slow down your desktop or laptop, because it will be using the full 100% processing power from the graphics cards and the central processing unit. This will later bring down the life scale of your device.
How to prevent CoinHive?
CoinHive is a Malware software that is based on JavaScript. If you really need to visit a website that is affected by CoinHive and blocked by the anti-virus, give permission to your anti-virus software to allow an access for this website, but at the same time, use external software to turn off JavaScript for this website and the mining software will not function while you are on it. I recommend using Malwarebytes premium version, because it is very helpful preventing such websites to mine on your computer without your permission and damaging your hardware. Malwarebytes has helped millions of people preventing such viruses and malwares. Most adblocker apps on browsers block CoinHive by default as well, so that can be a free solution to prevent webpages mining on your computer without your permission.
How does CoinHive work?
It operates on JavaScript miner for the Monero blockchain. It is embedded onto websites by the attacker. Once websites are visited, it will use your system to mine for itself. Some websites (which are targeted) allow you to download various content. People who don’t know about the malware on the website, will download and use the content on their systems. The content they downloaded from the infected website might also contain a Malware mining system, which will also mine on their device, even though they are not on the website anymore. The mined currency will be then sent back to the attacker through a cloud or a direct system. Web pages which intentionally use CoinHive must notify their audiences before they have full access to their websites. Sadly, most of them don’t notify the audiences about this matter.
References:
https://www.wired.com/story/cryptojacking-cryptocurrency-mining-browser/
https://blog.malwarebytes.com/security-world/2017/10/why-is-malwarebytes-blocking-coinhive/
https://arstechnica.com/information-technology/2017/10/a-surge-of-sites-and-apps-are-exhausting-your-cpu-to-mine-cryptocurrency/
https://www.pcmag.com/news/357535/why-hackers-love-cryptocurrency-miner-coinhive
https://www.howtogeek.com/334018/how-to-block-cryptocurrency-miners-in-your-web-browser/
https://lifehacker.com/how-to-stop-sites-from-harvesting-cryptocurrency-from-y-1819712943
https://www.theregister.co.uk/2017/10/19/malwarebytes_blocking_coin_hive_browser_cryptocurrency_miner_after_user_revolt/
Cem Gurkan
Other interesting articles
All news


