
12 August 2021 / 5 minutes of reading
3 Cybersecurity Essentials That Actually Make a Difference
Data breaches are on the rise — but the good news is, you don’t need advanced tools to protect yourself. Start with these three essentials.

Cases of leaked data and malicious attacks have rapidly increased over time. When hackers get access to your devices, they can easily steal your identity, money or threaten to disclose sensitive data which could tarnish your reputation.
To prevent these kinds of threats, we suggest applying these 3 basic security principles:
1. Use a password manager
A password manager is a tool to keep track of all of your passwords. It’s the only way to create unique passwords for all of your accounts and be able to remember them with ease. There are two types of solutions depending on where the tool stores the data. One of them stores all of the data in the cloud and the second stores data locally on your personal device.
If you use the same password for all your accounts because you're afraid of forgetting, the chances that a hacker will successfully attack you highly increases. It is an all too common, but dangerous habit. To avoid this, you can use a password manager to remember all of your unique, and ideally strong, passwords. All that you need to do is choose a password to access the password manager. What is the best way to do that? We recommend that you use a "passphrase" - a series of unique words, that when combined, make sense to the user and is easier to remember. More on "Passphrases" can be found here, which might just help you create a safe passphrase. This then becomes the only password that you have to remember. It allows you to access the password manager where all of your passwords are safely stored.
Alternatively, a password can be created by a password generator, as seen below:
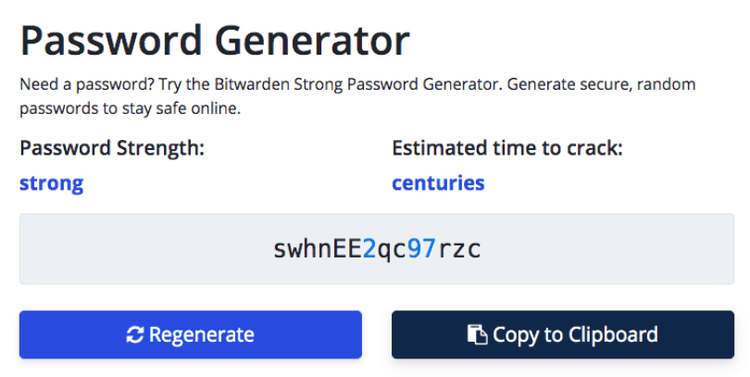
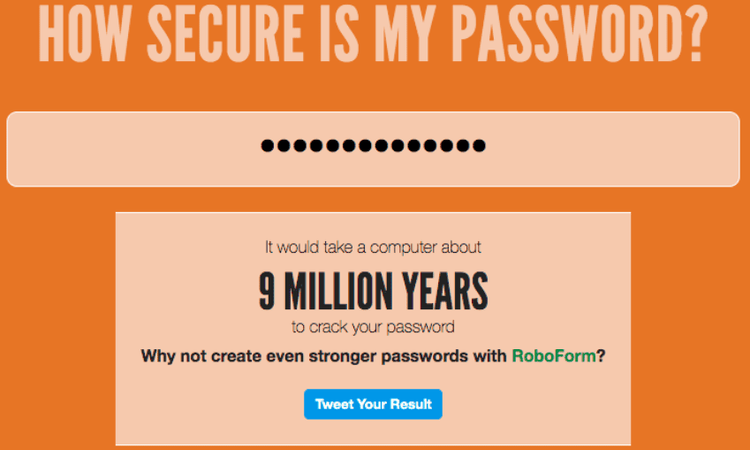
You can also use the website “How Secure is my password” to check how long it would take a computer to crack your password. As you can see in the next picture, the password above would take 9 million years to crack.
This is a rough estimate (common words or commonly used phrases can be in dictionaries with which the password is cracked). Also, the application claims that the passwords are not sent anywhere using this application.
You can find many different types of password managers, with a bunch of additional services and features that they provide. Generally though, a password manager should have 2 main features:
- Securely store passwords
- Securely generate passwords
There are plenty of password managers to choose from. If you prefer to use an online tool, take a look at apps such as , Bitwarden, or Onepass. For offline tools, consider KeePass and KeePassXC. To find more password manager options, read this article about the comparison of password managers.
2. Using two-factor authentication (2FA) is essential
2FA (Two-factor authorization) is an extra layer of security that is used to verify a user who is attempting to access an application. Users have to provide two different authentication factors to verify themselves. We recommend using 2-factor authentication to access applications where you store any sensitive data.
Here are two common types of authentication:
- SMS/Text-Message
During the login process, the user automatically receives an SMS, containing a unique numerical code, directly to their mobile number. This "token-code" is then entered by the individual, verifying themselves as the user that is attempting to log into the online account. This process significantly reduces the ability for online data to be compromised, as only the user with the linked phone number will be able to access the account at the time. Using the SMS 2FA is better than nothing, however, attackers still have some possible methods such as SIM scams, phone theft, etc for stealing your data. Therefore, we strongly recommend having apps for 2FA verification.
- Apps for 2FA verification
These apps can send the user a notification that an authentication attempt is taking place. The user simply views the details and can approve or deny access with a single action. The authentication is passwordless, with no codes to enter and no additional interaction required. There are quite a few apps for 2FA verification such as Authy, Google Authenticator, and Last Pass, to name a few. To compare those apps, check out The best 2FA apps of 2021.
3. Communicate through secure & trustworthy chat apps
When communicating or sharing any type of sensitive data, we strongly recommend avoiding chat apps that do not encrypt your data. This is especially true for apps that have recently faced data leakage scandals and those whose terms and conditions are questionable, to say the least.
Lastly, we recommend using apps that are end-to-end encrypted. Also, whenever possible, set a timer for messages to be automatically deleted. Signal or Threema may be a good fit for these needs.
Do you want to know more about how to work with a password manager? Stay tuned for more in our upcoming articles and blog posts!
Other interesting articles
All news


