
26 January 2018 / 5 minutes of reading
ExtendedMacro – BurpSuite plugin
BurpSuite Proxy is one of the most used HTTP proxy application for web penetration testers. This tool is one of the best in its category, but sometimes we encounter a situation requiring additional functionality which is not provided by Burp itself.

BurpSuite Proxy is one of the most used HTTP proxy application for web penetration testers. This tool is one of the best in its category, but sometimes we encounter a situation requiring additional functionality which is not provided by Burp itself. Fortunately, anyone is able to extend its functionality using various plugins.
Here are some typical examples of such situation: when doing request signing or doing several requests before/after a specific user action; user session renewal, CSRF token retrieval or filling up multi-step forms. Such functionality is partially supplied by built-in Burp Macro; however, it does not provide functionality such as adding new HTTP headers. Therefore, we decided to develop a custom extension providing extended functionality.
Our plugin can be installed directly from the Bapp store Bapp Store on it can be downloaded from GitHub. It uses MIT license.
Functionality description
The main functionality is the ability to execute one or more requests before each request is triggered from any Burp tool like Proxy, Repeater, Scanner, Intruder, Sequencer or Spider. These requests can be sent every time or once per given time interval. This plugin gives an opportunity to extract data from requests and puts them in the following requests (e.g. request a CSRF token, extract the token value from the response and add it to next request’s HTTP header).
Features:
- create sequence of request(s) to be sent before every request done manually or by other Burp tools
- extract data from responses
- paste extracted data to following requests (replacement of existing data, add new HTTP header, replace existing HTTP header value)
- changing requests order
- URL decoding of extracted data
- extracted data caching (specify time interval when the extraction is performed)
Extra features not provided by BurpSuite Macro:
- ability to replace arbitrary string in a request
- ability to add a new header into a request
- simpler configuration
- extracted data caching
User interface
The ExtendedMacro plugin creates new tab “Extended Macro” in the Burp panel bar. In addition, a new context menu item is added to the application – “Send to ExtendedMacro”. The plugin consists of 3 main tabs:
- „Main“ – main functionality
- „Logger“ – history of requests and responses
- „Settings“
Main
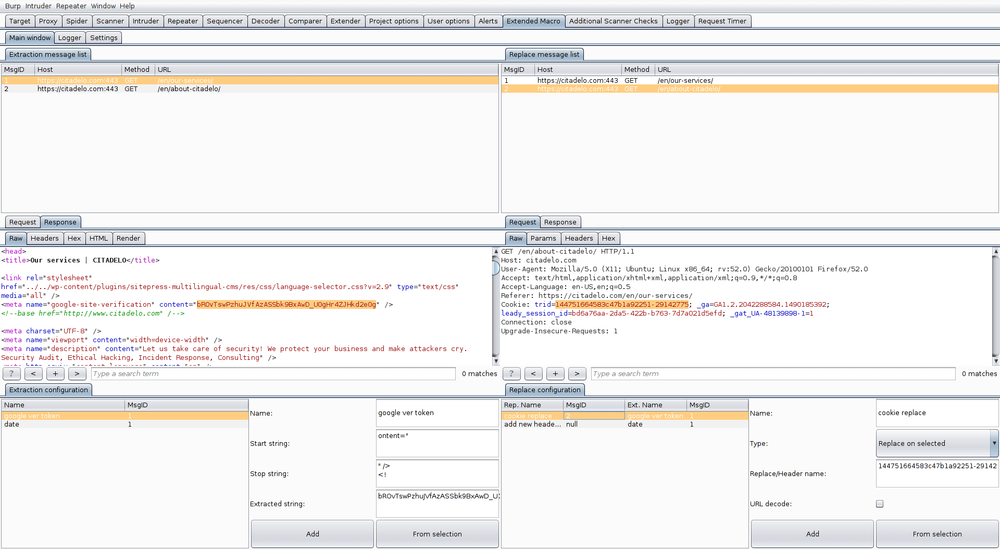
Main tab provides the core functionality of the plugin. It shows a list of all requests and which data are extracted and replaced. The left panel is used for an extraction configuration – section “Extraction message list”. The right panel has a configuration of where extracted data is put – section “Replace message list”.
„Extraction message list“
Here the queue of requests is shown. Using the right mouse click, you can display context menu providing options to change order of the requests or to remove requests.
After selecting the request, its content is displayed in the request/response editor. In the response editor, we can select which data should be extracted. The button “From selection” creates an extraction rule in the “Extraction configuration” panel. Now, we only need to set a name and click on “Add” button. As a result, the new extraction rule is added to the list.
„Replace message list“
Here you can view and set rules on how to process extracted data. First, you need to create an extraction rule. Extracted data defined by the rule can be put to an arbitrary following request from the same list or to any request from an arbitrary Burp suite tool.
Logger
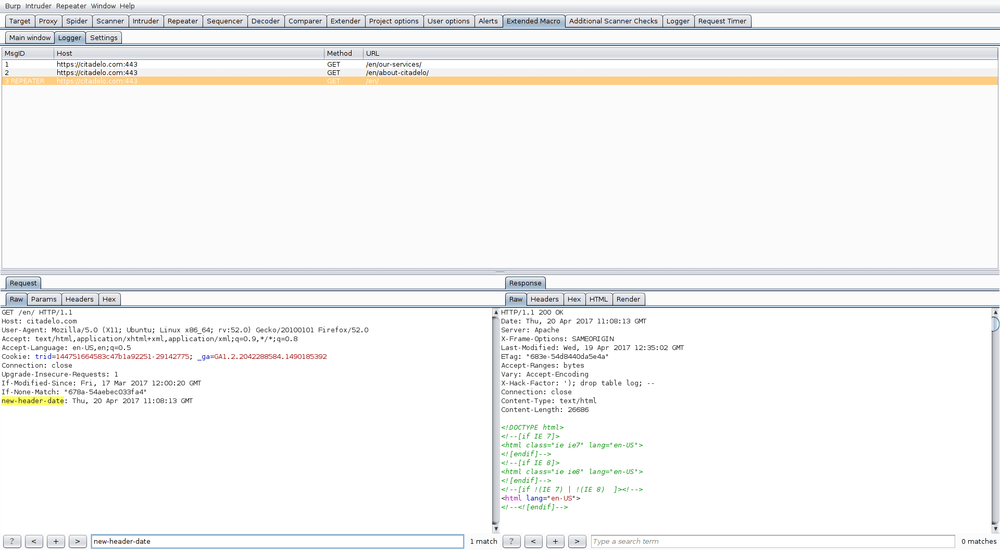
The logger shows all requests done by every Burp tool, including requests done by the Extended Macro plugin. This is very helpful for debugging and making sure that the extraction configuration works as intended
Settings
In the Settings tab, you can set up which Burp tools are affected by Extended Macro plugin (available options are Repeater, Scanner, Spider, Intruder, Sequencer or Proxy). If a specific Burp tool is unselected, the requests defined in the plugin configuration will not be sent prior tool own requests. Furthermore, you can set up an interval of extracted data caching.
Usage example – request a CSRF token, extract value and put it to the Burp tool request
- Select a request (from Proxy) giving us a new CSRF token, click the right mouse button and select “Send to ExtendedMacro”
- Open ExtendedMacro and select our request in “Extraction message list”
- Select data in the response editor – in our case, this is CSRF token value
- Click on the “From selection” button, which creates an extraction rule (it specifies definition of the range – start and stop string)
- Set a name and click “Add” button in “Extraction configuration” – a new rule is created in the list with associated message ID
- On the right side in “Replace configuration”, select “Replace header in Burp request” type – this changes or adds a new HTTP header
- Put “Anti-CSRF-Token: “in the “Replace/Header name”
- Select your extraction rule in “Extraction configuration” on the left
- In “Replace configuration” section on the right, set a name and click “Add” button – it creates the rule which updates the HTTP header
- Now, you can test this configuration e.g. using Repeater tool and then verify that it works in the Logger tab, where all requests will be visible
Other interesting articles
All news


