
28 January 2018 / 3 minutes of reading
Unofficial Patch Tuesday – MSMQ Privilege Escalation Vulnerability Hotfix
Microsoft won’t patch this one — so we did. CVE-2014-4971 is a known privilege escalation vulnerability in the MSMQ service on Windows XP. Citadelo’s unofficial hotfix helps secure legacy systems against this active exploit.

This security patch resolves a public vulnerability in the Windows Message Queuing Service (MSMQ) discovered by KoreLogic [1]. By default, the Message Queuing component is not installed and only Windows XP is affected. Since Microsoft stopped releasing security patches for Windows XP [2] and an exploit module is available in Metasploit [3], We have decided to release a Hotfix for this vulnerability to protect Windows XP users. The patch has been successfully tested on Windows XP SP3 and doesn't contain any malicious content.
UPDATE: The original version of the patch is not compatible with the /3GB boot parameter. The current version is compatible with the /3GB boot parameter. We would like to thanks to Mr. Patrik Horník from technology news site DSL.sk for reminding.
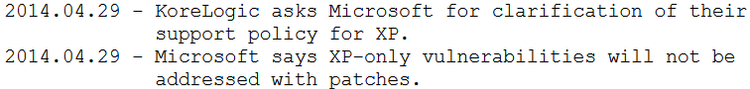
Microsoft doesn't plan to patch this vulnerability (from KoreLogic advisory):
How to apply a patch
1. Boot Windows XP in Safe mode [4]
2. Run python script(patch) [5]
Patch
``` #!/usr/bin/python # # MSMQ Privilege Escalation Vulnerability Hotfix - CVE-2014-4971 # 12th August 2014 - Alino from Citadelo - [email protected] # # Disclaimer: Use this security patch at your own risk.
import os import sys import ctypes import shutil import hashlib import platform
original = "7849c06480eeb96c0d06689e5db80ddcacc5dd077ce6dfa25ccb7bdf3378c962" patched = "b014b913a1f913fad4d15cce9b27ff2b54f6f015c768b622c2baf049ca5f5b2e" old_patch = "f481a1c6ea8508854ee8b4051d423679d58abb66586d904c7240b200fb109432"
driver = os.environ['WINDIR'] + "\System32\drivers\mqac.sys" driver_bck = os.environ['WINDIR'] + "\System32\drivers\mqac.bck"
print "\n[] MSMQ Privilege Escalation Vulnerability Hotfix - CVE-2014-4971" print "[] 12th August 2014 - Alino from Citadelo - [email protected]"
if platform.release() != "XP": sys.exit("\n[-] ERROR: This patch is for Windows XP!")
if ctypes.windll.user32.GetSystemMetrics(67) == 0: sys.exit("\n[-] ERROR: Must be run in Safe mode!")
if ctypes.windll.shell32.IsUserAnAdmin() != 1: sys.exit("\n[-] ERROR: You must have Administrator rights!")
if not os.path.exists(driver): sys.exit("\n[-] ERROR: Driver mqac.sys not found!")
hasher = hashlib.sha256() with open(driver, "rb") as file: buffer = file.read() hasher.update(buffer)
if hasher.hexdigest() == patched: sys.exit("\n[-] ERROR: Already patched!")
if hasher.hexdigest() != original: if hasher.hexdigest() != old_patch: sys.exit("\n[-] ERROR: Wrong driver version! This patch is for version 5.1.0.1110")
shutil.copyfile(driver, driver_bck) print "\n[*] Backup file mqac.bck created"
buffer = buffer[:0x138] + "\x0A\xE1\x01" + buffer[0x13B:] # PE CHECKSUM buffer = buffer[:0x1EFA] + "\xE9\xDD\x18\x01\x00" + buffer[0x1EFF:] # JMP mqac!_alldiv+0x6 buffer = buffer[:0x1F32] + "\xEB\xC6" + buffer[0x1F34:] # JMP mqac!AC2QM+0x20 buffer = buffer[:0x137DC] + "\xE8\x00\x00\x00\x00\x5B\x8B\x5B\x73\x8B\x1B\x3B\xF3\xBB\x00\x00\x00\x00\x0F\x83\xE2\xE7\xFE\xFF\xE9\x3B\xE7\xFE\xFF" + buffer[0x137F9:] # CALL mqac!_alldiv+0xb; POP EBX; MOV EBX,DWORD PTR [EBX+73h]; MOV EBX,DWORD PTR [EBX]; CMP ESI,EBX; MOV EBX,0; JNB mqac!AC2QM+0xfc; JMP mqac!AC2QM+0x5a
f = open(driver , "wb") f.write(buffer) f.close()
print "[*] Driver sucessfully patched!"
<p>Metasploit module will fail with patched driver:</p>

<p><strong>Disclaimer</strong></p>
<p>Use this security patch at your own risk.</p>
<p>Stay secure,<br /> Alino, [email protected]</p>
<p>References:<br />1. <a href="https://www.korelogic.com/Resources/Advisories/KL-001-2014-003.txt">https://www.korelogic.com/Resources/Advisories/KL-001-2014-003.txt</a><br />2. <a href="http://windows.microsoft.com/en-us/windows/end-support-help">http://windows.microsoft.com/en-us/windows/end-support-help</a><br />3. <a href="http://www.rapid7.com/db/modules/exploit/windows/local/mqac_write">http://www.rapid7.com/db/modules/exploit/windows/local/mqac_write</a><br />4. <a href="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/boot_failsafe.mspx">http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/boot_failsafe.mspx</a></p>
Other interesting articles
All news


